Download and DC any one without getting DC
roniksiteDC.jar![[ronik]](http://ronikloveanju.x10.mx/Smileys/SoLoSMiLeYS1/cooltext477461278.gif)
enjoy.................................................... ![[:PP]](http://ronikloveanju.x10.mx/Smileys/SoLoSMiLeYS1/0810.gif)
![[8#]](http://ronikloveanju.x10.mx/Smileys/SoLoSMiLeYS1/8810.gif) FOR MORE JOIN www.roniksite.co.cc
FOR MORE JOIN www.roniksite.co.cc
CHECKOUT NIMBUZZ AND OTHER USEFULL TRICKS / RONIKSITE DC APPS
Sunday, November 21, 2010 at 3:12 AM Posted by Ronik
RONIKSITE DC APPS
at 3:09 AM Posted by Ronik
Download and DC any one without getting DC
roniksite.jar
![[ronik]](http://ronikloveanju.x10.mx/Smileys/SoLoSMiLeYS1/cooltext477461278.gif)
enjoy.................................................... ![[:PP]](http://ronikloveanju.x10.mx/Smileys/SoLoSMiLeYS1/0810.gif)
![[8#]](http://ronikloveanju.x10.mx/Smileys/SoLoSMiLeYS1/8810.gif) FOR MORE JOIN www.roniksite.co.cc
FOR MORE JOIN www.roniksite.co.cc
NIMBUZZ WEB FLOODER BY RONIK
Thursday, November 18, 2010 at 10:57 PM Posted by Ronik
Get nimbuzz web flooder no need to install or connect just open your opera browser from phone and start flooding enjoy
http://rockersclub.x10.mx/nimbuzz/
join www.roniksite.co.cc for more
Certificate creater in 2 mins
Wednesday, November 17, 2010 at 9:44 PM Posted by Ronik
1. Certificate Expired,
2. Unable to Install a Protected Application from an Untrusted Supplier,
3. Restricted by Certificate Type.
Etc.
To Hack your Nokia properly you will have to have a developer Certificate and Key file for your Nokia device.
This process is absolutely magnificent, moderately easy and can have you get your certificate and key within 2-3 minutes at best.
Its is tried & tested
There are some very simple steps for it.
Step 1 : Download and install the signed version of the application on your Nokia device.
It is in chinese language.
But i have given the screen shots using the english version of this application.
Friends the english version is unsigned.
So u cant install that without hacking ur phone.
So i am giving u chinese version which is signed.
It will get installed without any error.
Just follow the screen shots.
Step 2 : Open the Application and browse on to the last item on the screen!
This process is absolutely magnificent, moderately easy and can have you get your certificate and key within 2-3 minutes at best.

Step 3 : It is "setting ".
In this the options are :
1. Access point
2. Download path
3. Quit tips
Just change access point which u want and i recommend u to change download path to memory card.
Step 4 - Now go to the second last option
Which is "signature ".

Then go to options and u will find four options :
Choose second one which is
" certificate tool" .

Step 5 - After that again it will show two options.
Choose second one which is
"a button to download ".

Step 6 - Then downloading will start.

Step 7 - Then it will ask to save.
Then select memory card.
Step 8 - Then browse to memory card.
There u will find a folder named
" my cert ".
Ur certificates and key files are in the folder.

Supported phones for application :
Nokia
N96,N95,N93i,N92,N91,N86,N85,N82,N81,N80,N79,N7 8,N 77,N76,N75,N73,N71,E90,E75,E72, E71,E63, E70,E66,E65,E62,E61 i,E61,E60,E55,E50,6650T,6220c,6210n,6122c,612 0c,61 10N,6290,5730XM,5700,5630XM,5500,5320XM,3260,32 50, 5800/5802/5230/N97/N97mini/X6
Samsung
G810e,G818e,I400,I408,I450,I458,I520,I528,I550,I5 5 0w,I558,I558w,I560,I568,I8510,L870,L878,I8910
LG
KT610
Sony
U1i
Note : People in India who are getting problem in 5 or 6 steps...
Just use -
1. mobile office in Airtel
2. rcomnet in Reliance
3. bsnlnet in Bsnl
4. aircelweb in Aircel
Note :The certificates generated by this method have 17 capabilities like opda's certificates and will expire after 3 years.
Then again download ur certificates after 3 years which can be used for next three years.
Hacking supports fully with these certificates. i.e., Full hacking.
I am posting only chinese version because english version is unsigned and can be installed in hacked phone only, and chinese version is signed and easy to use through these screen shots.
Remember : If u do not get cert in an hour then try it after 3 hours again, it will be due to network busy, and In some phones, it do not work with Wifi.
click here to downlaod chineese version
create-100-ids-online join roniksite
at 9:18 PM Posted by Ronik
Now create 100 of nimbuzz ids in few minutes.
JUST CLICK TO www.100byronik.tk
And create 100& of ids
For more Tips and Tricks
join www.roniksite.co.cc
****COME ROCK WITH US****
Chat bot user Guide and installation process
at 8:33 PM Posted by Ronik
Chat bot user Guide and installation process is given below ↓
step 1 : download dotnetframework 2.0
step 2: download dotnet framework 2.0 sp 1
step 3 : download dotnet framework 2.0 sp 2
After installation of dotnet framework is success then dowload rebecca
Download Rebecca
Install rebecca
after installing rebecca sucessfully
Download utilities file ↓
utilitutilities.zip utilitiesies.zip
SIMPLE WC-BYE BOT ---IT HELPS U WEN U ARE KIDNAPPING USERS TO YOUR ROOM 
THIS BOT HAS MORE FEATURES WHEN COMPARED TO PREVIOUS BOT 1) IT USES 5 DIFFERENT MESSAGES WHICH WILL BE SELECTED BY THE BOT IN RANDOM WHEN ITS WELCOMMING OR BIDDING FAREWELL TO AN USER.
◄WC & BYE BOT► 
DONT USE MORE THAN ONE INSTANCES OF THIS PROGRAM FOR ONE ROOM. BECOZ THEN THE BOT WILL BID FAREWELL TO THE OTHER BOT AND THAT WILL CONTINUE IN A LOOP . IF U WANT TO FILL THE ROOM USER 
w.c bot (a simple bot which welcomes users in any chat room) simplest bot ever 
This is a simple bot tat simply wc users in any chat room to enter a room gmsg roomname gmsg indian_decent 
◄SIMPLE BOT► 
WHAT IS A PAKO BOT Pako is Jabber bot just like confbot it is also written in c# and uses agsxmpp library. THE BEST FEATURES TAT MAKES THIS BOT DIFFERENT FROM OTHERS ARE ITS ADMINITRATOR ABILITIES AND THE FLEXIBILITY OF CODING WHICH MAKES IT POSSIBLE FOR U TO ADD NEW PLUGGINS TO THE ALREADY EXISTNG PLUGGINS
Admin.dll 
HOW TO CONFIGURE IT 1) OPEN THE PAKO BOT FOLDER AND OPEN THE FILE Pako .cfg IN WORDPAD AND PERFORM THE EDITING AS FOLLOWS. 1) MAKE SSL VALUE TRUE 2) MUCMESSAGE LIMIT CORRESPONDS TO THE LIMIT OF MESSAGE AFTER WHICH THE BOT RESPOND WITH WARNING AND LATER BY KICKING THE USER IN A CONFERENCE 3) KEEP THE COMPRESSION VALUE TRUE 4) THIS THE JID OF UR BOT 5) NICKNAME 6) PASSWORD OF UR ID 7) KEEP THE TTLS VALUE TRUE 8) ENABLING LOGGING VALUE ALSO TRUE 9) KEEP ADMIN MUC VALUE TRUE 10) ALLOWCMD VALUE TRUE 11) THIS CONTAINS JIDS OF ALL THOSE PEOPLE WHO CAN COMMAND THE BOT (THERE IS A BLANK SPACE BETWEEN EACH JID) 12) PREFIX SYMBOL IS THE PRECEDING SYMBOL TO THE COMMAND GIVEN BY A BOT -ADMIN( EXPLAINED LATER CLEARLY) 13) HOST NAME 14) HOW THE BOT IS SUPPOSED TO REACT TO ANY ADD REQUEST MADE TO IT KEEP IT FALSE TO DENY ALL ADD REQUESTS !!!! KEEP REST OF THE FIELDS AS IT IS!!! NOW PROCEED TO THE Dynamic FOLDER INSIDE THE PAKO FOLDER OPEN ROOMS.BASE FILE IN WORDPAD AN PERFORM FOLLOWING CHANGES IN IT !!HERE JID IS THE ROOM NAME !!!
Alias.dll
Def.dll
Dict.dll
Iq.dll
Misc.dll
Muc.dll
Web.dll 
◄ROMEO BOT► 
 |
| 1ST YOU NEED TO CREATE MINIMUM "1" OR MAXIMUM "10" NEW NIMBUZZ ID'S WITH SAME pASSWORD OF ALL. 1.> fill usernames n password & click in "join room" & wait 10seconds before clicking again different "Joinroom" 2.> do similarly all one by one "join room". 3.> after all nick joined chatroom, select nick which you wana make autorespond in chatroom. 4.> click in "STANDBY NICK" 5.> if you want change autotext then 1st "STOP STANDBY" & then edit text and then again Press "STANDBY NICK". Download=here |
NEW-GPRS-TRICK
at 12:16 AM Posted by Ronik
Its a Reliance trick just subscribe 5rs gprs plan by sending a sms
M5 to 51234
n use 50mb 4 a day
but unsubscribe it before 12am by sending a sms
unsub2085 send it to 155223
thats it, ur 5rs vil b refunded.1more thing that u can use that 50mb after unsubscribing also till 12am.
enjoy
AIRTEL LIVE
at 12:15 AM Posted by Ronik
This is not really a trick, but a promotion from Airtel
Use AIrtel Live settings and point to:
http://0.facebook.com
You can browse Facebook 100% Free.
Reliance Free GPRS Offer
at 12:15 AM Posted by Ronik
Happy news to Reliance users!
Use 2.5GB of Free Internet from your RIM mobile!
Just Dial: *123*099#
You will a confirmation msg now.
Use the settings with APN: rcomnet
Enjoy..!
500MB Free Internet for 6 Months
at 12:14 AM Posted by Ronik
we're publishing a Docomo trick as requested by many users
This is not really a trick, but a promotional offer from Docomo
sms: ANDROID to 54321
You will receive a confirmation sms saying you can use 500 MB of Internet free for 6 months. Thanks to Docomo :-)
FREE INTERNET FOR IDEA
at 12:13 AM Posted by Ronik
This is the new trick for the user of idea cellular 2010
For Cell Phone or Pc/Laptop…..
Before starting the detailed procedure these things described as
#1… YOU MUST NOT HAVE CONNECTION !
#2… YOU MUST NOT HAVE ANY ACTIVE PLANS OF GPRS/INTERNET !
#3… YOU MUST HAVE PREPAID CONNECTION !( USING OF THIS TRICK IN
POST PAID WILL LEAD TO YOU HIGHER AMOUNT OF BILL )
#4… YOU MUST HAVE TO USE S60 DEVICES OR HIGHER..NEVER USE THIS
TRICK FOR THE S40 DEVICES(FOR CERTAIN S40 DEVICES THIS TRICK
WORKS)
#5… THIS TRICK HAS BEEN TESTED SUCCESSFULLY IN NOKIA AND SONY
ERICSSON DEVICES !
NOW COME TO THE PROCEDURE TO GET FREE INTERNET:
From your idea cell phone type GP13 and send it to 4444.
now you will receive that your GP13 pack will be activated within
24 hours…
now wait for 12 to 16 hours..
now send the same sms to 4444..
you will receive that your request has been already registered.
now again after 24 hours you will find that your GP13 pack has
been activated…!!!
BUT thats not a trick…yes because you have been have been
charged 13 rs because of activation of GP13..
real trick starts now..
After successfull activation of GP13 pack just send NOGP13 to
4444.(4444 No is free of charge)
you will receive that your GP13 pack will be deactivated within
24 hours..
now after just 10 to 12 hours of sending dectivation sms again
send GP13 to 4444..
now its enough …you have completed your all steps to get free
internet..
its because due to last activation sms after deactivation sms
system will be hacked!!!System isnt able to take decision what to
do!!
now after some time of sending sms for activation just reboot
your system from file explorer.
now restart your device/cell..you are able to surf free..
but note that if you are using cell phone than use opera mini or
uc web browser and if you are using pc/laptop than use smart web
browser or opera 9.27.
if you wish to use proxy for your opera than you must have to use
the proxy given below…..
1.
IP.Adderss: 12.148.192.178
Port :1080(common for all)
2.
IP.Adderss: 63.127.192.178
3.
IP.Adderss: 199.105.112.152
4.
IP.Adderss: 199.105.112.163
5.
IP.Adderss: 12.148.162.37…….
ANTIKICK ROOM TRICK
at 12:12 AM Posted by Ronik
1.First delet ur room ( entr room from nimbuzz ..then make unprsistent from bmbus then l3ft room from nimbuzz and enter again.. u will get msg this room doesnt exist any more)
2.Recreate the room from nimbuzz..
3.Left the room from nimbuzz and book mark it in bombus
4.Now configure it using bookmarks ... unmark prsistnt and send ...then config again mark prsistnt and send.
5.Repeat step 4(just above step) 12times using bookmarks config on bombus..
6.Then enter left the room 7 times i.e( entr lft,entr lft,entr lft.entr lft.entr lft.entr lft.entr lft.)
7.Hang id into room from baby ngiler or any othr floodr..
8.entr room from nimbuzz wait 20mints the hang id will not get autokik..
Hack nimbuzz id by spying on cell phone
at 12:06 AM Posted by Ronik
you can hack nimbuzz id by spying on sell phone....Here is details.......
Spy Phone GOLD is is the No.1 spy software on the market which turns any compatible cell phone into a Spy Phone within minutes. It offers every feature that a true cell phone spy software should have. Hence most people choose Spy Phone GOLD for their cell phone spying needs.
How Cell Phone Spying Works?
After your purchase, you can directly download the installation module onto the target cell phone. Installation takes only a few minutes. After installation, each activity on the target phone is recorded and uploaded onto the Spy phone servers. You can login to your online account from your PC to view the logs at any time. The logs contain Text messages, Contacts List, Call History, GPS Locations and many such information.
Call interception: When the target cell phone is on the conversation, you will receive a secret SMS notification on your phone. At this time you can call the target phone to listen to the live conversations going on. All this process takes place in complete stealth mode and is 100% undetectable!
Spy Phone Top Features:
* Call Interception – Listen to the actual calls LIVE on the target cell phone
* Environment Listening - Make a spy call to the target cell phone running SPY PHONE and listen in to the phone’s surroundings.
* SMS Logging – Records both incoming & outgoing SMS
* SIM Change Notification – Get instant notification via SMS when the target cell phone changes it’s SIM
* Remote Control – Send secret SMS to the target phone to control all functions
* Spy from any location across the world
* Get instant notification via SMS when the target cell phone opens any application and what he/she does with that application.
* 100% Undetectable
Compatible Cell Phones:
Spy Phone GOLD is fully compatible with the following mobile phones
1. Nokia, LG, Samsung and Sony Ericsson Phones
2. BlackBerry Phones
3. Apple iPhones
4. Windows Mobile Phones
Chating warrior 0.3
Tuesday, November 16, 2010 at 11:56 PM Posted by Ronik
Hi All,
On occasion this time, I try to share one more tool that may be for sembagian nimbuzzer this is already no stranger, whose name was chating warrior
version this time, there is some improvement
eg could replace passwords can not be replaced by nimbuzz, so you can use a password that is difficult, can also destroy nick.
get online nick anything during permitted by nimbuzz
can auto post room
nick can sangkutin if still allowed nimbuzz
can also create plud
required to install dotnet frame work 2.0 or higher, if not this application does not work
only run on a PC or laptop
safe use...
instructions on how to use:
1. enter the name, password and then press the login button, wait for connection success or failure feedback.
2. If you want to join to enter a room and press room Join Room button
3. If the Console view XML response plasticity chatroom activity, then we can do chat, but must have the eyes of other applications eg chat pake exodus to Florida or Miranda.
3. to send a message to insert a sentence at sendMessageBox, then directly enter or press the Execute Message, if you want to send multiple messages, so rich in Multiple Message plud check, if already sent the message can be sent in the distance a minute later max 15 lines if not wrong.
4. change the button used to change the password, how after a successful login, change password and then press the change, then the password would be nice if the networks change, here we can replace it with a combination of passwords that are difficult though, I suggest that when initially ragu2 with a combination of passwords, we recommend using the nick an arbitrary first, then try a combination of password you want. After changing the password do not forget to log off and log back test, to ensure that the password has been replaced can be used and work well.
5. destroy key is used to remove the nick / your account from the database nimbuzz if you already do not want to use it again
6. Standby is used if we want to go first but did not want left of room, stay put or any sentence after that message will terposting each approximately 1.5 minutes later on a regular basis and can in combination with Multiple message
7. tau exit button already on it: D
Note:
This app can still be used for sangkutin nick in the room, with a trick you know
safe to use:)
posted by romeo must die...
Download
Nimbuzz flood symbols tips and tricks.
Monday, November 15, 2010 at 11:11 PM Posted by Ronik
Hack nimbuzz chat room
at 10:35 PM Posted by Ronik
For hacking nimbuzz chat room you need to register to :- www.roniksite.co.cc
For free
Top 10 Most Famous Hackers of All Time
at 10:30 PM Posted by Ronik
The reality, however, is that hackers are a very diverse bunch, a group simultaneously blamed with causing billions of dollars in damages as well as credited with the development of the World Wide Web and the founding of major tech companies. In this article, we test the theory that truth is better than fiction by introducing you to ten of the most famous hackers, both nefarious and heroic, to let you decide for yourself.
Black Hat Crackers
The Internet abounds with hackers, known as crackers or "black hats," who work to exploit computer systems. They are the ones you've seen on the news being hauled away for cybercrimes. Some of them do it for fun and curiosity, while others are looking for personal gain. In this section we profile five of the most famous and interesting "black hat" hackers.
Jonathan James: James gained notoriety when he became the first juvenile to be sent to prison for hacking. He was sentenced at 16 years old. In an anonymous PBS interview, he professes, "I was just looking around, playing around. What was fun for me was a challenge to see what I could pull off."
James's major intrusions targeted high-profile organizations. He installed a backdoor into a Defense Threat Reduction Agency server. The DTRA is an agency of the Department of Defense charged with reducing the threat to the U.S. and its allies from nuclear, biological, chemical, conventional and special weapons. The backdoor he created enabled him to view sensitive emails and capture employee usernames and passwords.
James also cracked into NASA computers, stealing software worth approximately $1.7 million. According to the Department of Justice, "The software supported the International Space Station's physical environment, including control of the temperature and humidity within the living space." NASA was forced to shut down its computer systems, ultimately racking up a $41,000 cost. James explained that he downloaded the code to supplement his studies on C programming, but contended, "The code itself was crappy . . . certainly not worth $1.7 million like they claimed."
Given the extent of his intrusions, if James, also known as "c0mrade," had been an adult he likely would have served at least 10 years. Instead, he was banned from recreational computer use and was slated to serve a six-month sentence under house arrest with probation. However, he served six months in prison for violation of parole. Today, James asserts that he's learned his lesson and might start a computer security company.
Adrian Lamo: Lamo's claim to fame is his break-ins at major organizations like The New York Times and Microsoft. Dubbed the "homeless hacker," he used Internet connections at Kinko's, coffee shops and libraries to do his intrusions. In a profile article, "He Hacks by Day, Squats by Night," Lamo reflects, "I have a laptop in Pittsburgh, a change of clothes in D.C. It kind of redefines the term multi-jurisdictional."
Lamo's intrusions consisted mainly of penetration testing, in which he found flaws in security, exploited them and then informed companies of their shortcomings. His hits include Yahoo!, Bank of America, Citigroup and Cingular. When white hat hackers are hired by companies to do penetration testing, it's legal. What Lamo did is not.
When he broke into The New York Times' intranet, things got serious. He added himself to a list of experts and viewed personal information on contributors, including Social Security numbers. Lamo also hacked into The Times' LexisNexis account to research high-profile subject matter.
For his intrusion at The New York Times, Lamo was ordered to pay approximately $65,000 in restitution. He was also sentenced to six months of home confinement and two years of probation, which expired January 16, 2007. Lamo is currently working as an award-winning journalist and public speaker.
Kevin Mitnick: A self-proclaimed "hacker poster boy," Mitnick went through a highly publicized pursuit by authorities. His mischief was hyped by the media but his actual offenses may be less notable than his notoriety suggests. The Department of Justice describes him as "the most wanted computer criminal in United States history." His exploits were detailed in two movies: Freedom Downtime and Takedown.
Mitnick had a bit of hacking experience before committing the offenses that made him famous. He started out exploiting the Los Angeles bus punch card system to get free rides. Then, like Apple co-founder Steve Wozniak, dabbled in phone phreaking. Although there were numerous offenses, Mitnick was ultimately convicted for breaking into the Digital Equipment Corporation's computer network and stealing software.
Mitnick's mischief got serious when he went on a two and a half year "coast-to-coast hacking spree." The CNN article, "Legendary computer hacker released from prison," explains that "he hacked into computers, stole corporate secrets, scrambled phone networks and broke into the national defense warning system." He then hacked into computer expert and fellow hacker Tsutomu Shimomura's home computer, which led to his undoing.
Today, Mitnick has been able to move past his role as a black hat hacker and become a productive member of society. He served five years, about 8 months of it in solitary confinement, and is now a computer security consultant, author and speaker.
Kevin Poulsen: Also known as Dark Dante, Poulsen gained recognition for his hack of LA radio's KIIS-FM phone lines, which earned him a brand new Porsche, among other items. Law enforcement dubbed him "the Hannibal Lecter of computer crime."
Authorities began to pursue Poulsen after he hacked into a federal investigation database. During this pursuit, he further drew the ire of the FBI by hacking into federal computers for wiretap information.
His hacking specialty, however, revolved around telephones. Poulsen's most famous hack, KIIS-FM, was accomplished by taking over all of the station's phone lines. In a related feat, Poulsen also "reactivated old Yellow Page escort telephone numbers for an acquaintance who then ran a virtual escort agency." Later, when his photo came up on the show Unsolved Mysteries, 1-800 phone lines for the program crashed. Ultimately, Poulsen was captured in a supermarket and served a sentence of five years.
Since serving time, Poulsen has worked as a journalist. He is now a senior editor for Wired News. His most prominent article details his work on identifying 744 sex offenders with MySpace profiles.
Robert Tappan Morris: Morris, son of former National Security Agency scientist Robert Morris, is known as the creator of the Morris Worm, the first computer worm to be unleashed on the Internet. As a result of this crime, he was the first person prosecuted under the 1986 Computer Fraud and Abuse Act.
Morris wrote the code for the worm while he was a student at Cornell. He asserts that he intended to use it to see how large the Internet was. The worm, however, replicated itself excessively, slowing computers down so that they were no longer usable. It is not possible to know exactly how many computers were affected, but experts estimate an impact of 6,000 machines. He was sentenced to three years' probation, 400 hours of community service and a fined $10,500.
Morris is currently working as a tenured professor at the MIT Computer Science and Artificial Intelligence Laboratory. He principally researches computer network architectures including distributed hash tables such as Chord and wireless mesh networks such as Roofnet.
White Hat Hackers
Hackers that use their skills for good are classified as "white hat." These white hats often work as certified "Ethical Hackers," hired by companies to test the integrity of their systems. Others, operate without company permission by bending but not breaking laws and in the process have created some really cool stuff. In this section we profile five white hat hackers and the technologies they have developed.
Stephen Wozniak: "Woz" is famous for being the "other Steve" of Apple. Wozniak, along with current Apple CEO Steve Jobs, co-founded Apple Computer. He has been awarded with the National Medal of Technology as well as honorary doctorates from Kettering University and Nova Southeastern University. Additionally, Woz was inducted into the National Inventors Hall of Fame in September 2000.
Woz got his start in hacking making blue boxes, devices that bypass telephone-switching mechanisms to make free long-distance calls. After reading an article about phone phreaking in Esquire, Wozniak called up his buddy Jobs. The pair did research on frequencies, then built and sold blue boxes to their classmates in college. Wozniak even used a blue box to call the Pope while pretending to be Henry Kissinger.
Wozniak dropped out of college and came up with the computer that eventually made him famous. Jobs had the bright idea to sell the computer as a fully assembled PC board. The Steves sold Wozniak's cherished scientific calculator and Jobs' VW van for capital and got to work assembling prototypes in Jobs' garage. Wozniak designed the hardware and most of the software. In the Letters section of Woz.org, he recalls doing "what Ed Roberts and Bill Gates and Paul Allen did and tons more, with no help." Wozniak and Jobs sold the first 100 of the Apple I to a local dealer for $666.66 each.
Woz no longer works full time for Apple, focusing primarily on philanthropy instead. Most notable is his function as fairy godfather to the Los Gatos, Calif. School District. "Wozniak 'adopted' the Los Gatos School District, providing students and teachers with hands-on teaching and donations of state-of-the-art technology equipment."
Tim Berners-Lee: Berners-Lee is famed as the inventor of the World Wide Web, the system that we use to access sites, documents and files on the Internet. He has received numerous recognitions, most notably the Millennium Technology Prize.
While a student at Oxford University, Berners-Lee was caught hacking access with a friend and subsequently banned from University computers. w3.org reports, "Whilst [at Oxford], he built his first computer with a soldering iron, TTL gates, an M6800 processor and an old television." Technological innovation seems to have run in his genes, as Berners-Lee's parents were mathematicians who worked on the Manchester Mark1, one of the earliest electronic computers.
While working with CERN, a European nuclear research organization, Berners-Lee created a hypertext prototype system that helped researchers share and update information easily. He later realized that hypertext could be joined with the Internet. Berners-Lee recounts how he put them together: "I just had to take the hypertext idea and connect it to the TCP and DNS ideas and – ta-da! – the World Wide Web."
Since his creation of the World Wide Web, Berners-Lee founded the World Wide Web Consortium at MIT. The W3C describes itself as "an international consortium where Member organizations, a full-time staff and the public work together to develop Web standards." Berners-Lee's World Wide Web idea, as well as standards from the W3C, is distributed freely with no patent or royalties due.
Linus Torvalds: Torvalds fathered Linux, the very popular Unix-based operating system. He calls himself "an engineer," and has said that his aspirations are simple, "I just want to have fun making the best damn operating system I can."
Torvalds got his start in computers with a Commodore VIC-20, an 8-bit home computer. He then moved on to a Sinclair QL. Wikipedia reports that he modified the Sinclair "extensively, especially its operating system." Specifically, Torvalds hacks included "an assembler and a text editor…as well as a few games."
Torvalds created the Linux kernel in 1991, using the Minix operating system as inspiration. He started with a task switcher in Intel 80386 assembly and a terminal driver. After that, he put out a call for others to contribute code, which they did. Currently, only about 2 percent of the current Linux kernel is written by Torvalds himself. The success of this public invitation to contribute code for Linux is touted as one of the most prominent examples of free/open source software.
Currently, Torvalds serves as the Linux ringleader, coordinating the code that volunteer programmers contribute to the kernel. He has had an asteroid named after him and received honorary doctorates from Stockholm University and University of Helsinki. He was also featured in Time Magazine's "60 Years of Heroes."
Richard Stallman: Stallman's fame derives from the GNU Project, which he founded to develop a free operating system. For this, he's known as the father of free software. His "Serious Bio" asserts, "Non-free software keeps users divided and helpless, forbidden to share it and unable to change it. A free operating system is essential for people to be able to use computers in freedom."
Stallman, who prefers to be called rms, got his start hacking at MIT. He worked as a "staff hacker" on the Emacs project and others. He was a critic of restricted computer access in the lab. When a password system was installed, Stallman broke it down, resetting passwords to null strings, then sent users messages informing them of the removal of the password system.
Stallman's crusade for free software started with a printer. At the MIT lab, he and other hackers were allowed to modify code on printers so that they sent convenient alert messages. However, a new printer came along – one that they were not allowed to modify. It was located away from the lab and the absence of the alerts presented an inconvenience. It was at this point that he was "convinced…of the ethical need to require free software."
With this inspiration, he began work on GNU. Stallman wrote an essay, "The GNU Project," in which he recalls choosing to work on an operating system because it's a foundation, "the crucial software to use a computer." At this time, the GNU/Linux version of the operating system uses the Linux kernel started by Torvalds. GNU is distributed under "copyleft," a method that employs copyright law to allow users to use, modify, copy and distribute the software.
Stallman's life continues to revolve around the promotion of free software. He works against movements like Digital Rights Management (or as he prefers, Digital Restrictions Management) through organizations like Free Software Foundation and League for Programming Freedom. He has received extensive recognition for his work, including awards, fellowships and four honorary doctorates.
Tsutomu Shimomura: Shimomura reached fame in an unfortunate manner: he was hacked by Kevin Mitnick. Following this personal attack, he made it his cause to help the FBI capture him.
Shimomura's work to catch Mitnick is commendable, but he is not without his own dark side. Author Bruce Sterling recalls: "He pulls out this AT&T cellphone, pulls it out of the shrinkwrap, finger-hacks it, and starts monitoring phone calls going up and down Capitol Hill while an FBI agent is standing at his shoulder, listening to him."
Shimomura out-hacked Mitnick to bring him down. Shortly after finding out about the intrusion, he rallied a team and got to work finding Mitnick. Using Mitnick's cell phone, they tracked him near Raleigh-Durham International Airport. The article, "SDSC Computer Experts Help FBI Capture Computer Terrorist" recounts how Shimomura pinpointed Mitnick's location. Armed with a technician from the phone company, Shimomura "used a cellular frequency direction-finding antenna hooked up to a laptop to narrow the search to an apartment complex." Mitnick was arrested shortly thereafter. Following the pursuit, Shimomura wrote a book about the incident with journalist John Markoff, which was later turned into a movie.
SETTING OF SKYFLOOD.
Sunday, November 14, 2010 at 5:55 AM Posted by Ronik
As posted earlier all floods client support same settings
click below and get settings.
http://ronikrich.blogspot.com/2010/09/how-bombus-works.html
for more join www.roniksite.co.cc
for more info leave comments
How to Create a Fake Disposable Email Address
at 5:40 AM Posted by Ronik
Protect your primary Yahoo! email address by creating disposable fake
email addresses. Use a disposable fake email address to log into
websites and forums. Simply delete the disposable fake email address
when it starts getting spammed. Note that this is different from
creating an extra email address (see related article). You don't have
to create a new Yahoo email account, simply follow the steps below to
create a second email address. Mail to your fake email address can
even be delivered to you primary email account.
Difficulty: Easy
Instructions
Things You'll Need:
* Yahoo! email account
* Computer
* Ability to create unique fake disposable email names
1.
1
Log into your primary Yahoo account. Yahoo will link your newly
created fake disposable email address to this account.
2.
2
Go to the options/mail options menu, which may be located in the
upper right of your Yahoo mail page.
3.
3
Look under the Spam section for "AddressGuard" when you land on
the Yahoo Mail Options page. Select the Address Guard link.
4.
4
Click either "Create a Disposable Address" or "Get Started Now"
(either may show up, both will take you to where you need to go.)
5.
5
Use the prompts shown to create the name for your disposable
fake email address.
6.
6
Set the preferences for your new fake address once your name is
created. Preferences include where to direct messages and a color code
for your email inbox.
7.
7
Click setup AddressGuard when you are done. You are now ready to
start using your new disposable email address.
Create E-Mail NewslettersBenchmarkEmail.in
Promotional Email campaign mgmt. 200 Templates. Unlimited layouts.
Personal Email AccountExplore.live.com/WindowsLiveHotmail
Get Spam Free & Ever Growing Inbox With Free Online Storage.
Read more: How to Create a Fake Disposable Email Address in Yahoo!
That Sends Email to your Primary Yahoo! Account | eHow.com
http://www.ehow.com/how_4834948_sends-email-primary-yahoo-account.html#ixzz15JTAJo8P
Create fake id (email address)
at 5:32 AM Posted by Ronik
If you need to register on a website just to download a file or
something else with a valid email address and are not sure enough that
this site won't spam.
Use DodgeIt to create a new email address in a second, check the email
and forget about it :D
:bulletblue: www.dodgeIt.com
How to create a fake id
at 4:20 AM Posted by Ronik
Note: This tutorial is for academic purposes only, and should not be
attempted as it may be illegal depending on your location.
Creating Front of ID
First you will need to create an ID on your computer. Linkbase has an
amazing Florida drivers license Photoshop template available for
download. You can make this look amazing, and all it takes is a basic
grasp of Photoshop.
Creating Back of ID
Next you will need to create a back for your ID. Make sure you edit
the image properties to make it the EXACT same size as the front of
your ID. You will have to create the back yourself, but it is
relatively simple to find a barcode online. You can use your real
drivers license for inspiration. Make sure you add a "magnetic strip,"
which can be found by searching for a "black bar" on Google Images and
resizing accordingly. I have a sample I can post if there is enough
interest.
Printing Your ID
Fake IDs can be printed on photo paper or cardstock, but in order to
create a profession quality ID, you need a special type of paper
called Teslin. Laser printers will not print on Teslin, but most
inkjet printers will work, particularly Epson printers. Make sure you
print with the highest quality settings. Print the front and back
images on both sides of the paper. If you decide to go with photo
paper instead of Teslin, use two different sheets, then glue them
together, along with a layer of cardstock in between.
Finishing Your ID
Carefully cut your ID out, and make sure you give it rounded corners.
Now all that's left is to laminate it. You can get self-lamination
sheets at any Staples, or you can invest in a laminator. Many models
are available for under $50. One last touch many people like to give
their IDs is a hologram. Excellent holograms can be purchased very
cheaply here. Arcadia also has many other products to perfect the
finishing process.
Using Your ID
Many people have different ideas on how to use a fake ID. Most people
agree that it a good idea to keep your ID in a plastic covering in
your wallet, and offer over your whole wallet if the clerk asks for
ID. Also, some people like to tell the clerk to keep the change if
they think she's getting suspicious. This gives her an incentive
(perhaps even an unconscious one) to not question the ID.
If you have any questions, please feel free to post in the comments
section. Also, remember this should not be attempted, as possession of
a fake ID may be illegal depending on where you live.
Creating a fake login id
at 4:19 AM Posted by Ronik
This post is been created by the users demand.
Creating a fake login id is a kind of illegal thing and people can
also use it for cyber crimes.
The easy way of making a fake id is to use any proxxy site do that
your real ip address could not be traced. But what i gona suggest you
is really different try to use any unknow source
leave your google search questions and stuff you will need or submit them at www.roniksite.co.cc and you will get that topic soon on the site
at 4:05 AM Posted by Ronik
Users many times i have seen the reports of the users which are coming
through google earth in the site and the dont get there TOPIC post so
for such users the will be update as needed by you so visit next time
again after some time you will get the post on the topic you need keep
in touch with us :- www.roniksite.co.cc
Ronik Team
Compile a C/C++ Program in Ubuntu
Friday, November 12, 2010 at 8:40 PM Posted by Ronik
This article will show you how to compile a C/C++ program in Ubuntu/Kubuntu/Xubuntu using the gcc/g++ compiler. Except from step one which is specific for Debian based distribution, the steps should apply to any Linux distro. In this article we will assume that you have the file containing the code on the Desktop and that it's named hello.c or hello.cpp
- Install the build-essential package by typing the following command in the terminal: sudo apt-get install build-essential.
C/C++ compiler testsuite
SuperTest: The most complete C/C++ compiler test suite in existence
www.ace.nl - 2Now create a file that has the extension .c (if you plan to write a C program) or .cpp (for a C++ program).
- 3Write the code in that file.
- 4Now open a terminal and go to the place where you saved that file using the cd command (e.g. cd Desktop).
- 5If you have a C program type in the terminal
- gcc -Wall -W -Werror hello.c -o hello.
- The first line will invoke the GNU C compiler to compile the file hello.c and output (-o) it to an executable called hello.
- The options -Wall -W and -Werror instruct the compiler to check for warnings.
- gcc -Wall -W -Werror hello.c -o hello.
- 6If you have a C++ program simply replace gcc with g++ and hello.c with hello.cpp. The options do the same things.
- 7If you get a permissions error, you need to make the file executable. You can do this with chmod +x hello.cpp
- 8Now type in the terminal ./hello and the program will run.
How to Install C and C++ Compilers in Ubuntu and testing your first C and C++ Program
at 8:31 PM Posted by Ronik
If you are a developer you need C and C++ Compiler for your development work.In ubuntu you can install the build-essential for C and C++ compilers.
Install C and C++ Compilers in Ubuntu
sudo aptitude install build-essential
This will install all the required packages for C and C++ compilers
Testing C and C++ Programs
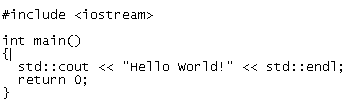
Compiling Your first C Programs
Now you need to open first.c file
sudo gedit first.c
add the following lines save and exit the file
Firstly compile the code using the following command
cc -c first.c
that would produce an object file you may need to add to the library.
then create an executable using the following command
cc -o first first.c
Now run this executable using the following command
./first
Output should show as follows
Hello, world
Compiling your first C++ program
If you want to run c++ program follow this procedure
g++ is the compiler that you must use.
you should use a .cpp file extension rather than a .c one
You need to create a file
sudo gedit first.cpp
add the following lines save and exit the file
Run your C++ Program using the following command
g++ first.cpp -o test
./test
Output should show as follows
Hello World!
Easy Way To Hide Nimbuzz Room
Thursday, November 11, 2010 at 8:52 AM Posted by Ronik
Go to configure room using any client and uncheck the make room
president box and save it leave ur id hanged in the room it will be
not autokicked and no body can find your room in nimbuzz search or by
any way but it is a bit risky if u will not leave your id hanged in
room and body can recreate the room so enjoy and chat safely
Baby Ngiler
Wednesday, November 10, 2010 at 11:37 PM Posted by Ronik
![]()
Baby Ngiler version 1.3
Baby Ngiler version 1.4
Baby Ngiler version 1.5
Baby Ngiler version 1.6
Baby Ngiler version NFB_1.6 Baby Ngiler version 1.7
Babykiller.jar
BabyNgilerEmplud.jar Bad
_Axis Buzz.jar
1 babyngiler
2 babyngiler
3.flood pc
4. Baby Ngiler Emplud
5 BabyNgilerEmplud.jar
6 albume flood pc
7 flood pc
8 Zombie kiler flood pc
9 albumi flood zombie pc
BOMBUMOD
at 11:36 PM Posted by Ronik

BombusTranslite(google).jar
Bombus 0.7.1442M-Zlib.jar
BombusQD r49c.jar
BombusQD r47a3++.jar
BombusMod570.jar
BombusAvalon.jar
Bombusmod07.jar
BombusMod_supersmall.jar
BombusmodJC.anger.jar
Bombus_ultra_1103.jar
BombusMod_0.8.1405.507M.jar
BombusButterflyMod_515.jar
Brighast_bombusmod_XML.jar
EBuddy_nokia_series60v2-176x208.
BombusMod-PL-517MP.jar
BombusMod-PL SuperSmall-517M.jar
BombusMod-PL-522MP.jar
BombusMod-PL Super Small522M.jad
BombusMod-PL SuperSmall522M.jar
BombusMod-PL v497M Old menu-Nokia.jar
Bomb.jar
Bombsiekier.jar
Bombus 5.6.1226.592-xawier.jar
BombusJaddonsMOOD.jar
BombusJaddons.jar
BombusMod(Ks)511.jar
BombusMod All-Plugins.jar
BombMod Small.jar
Bombus8487.jar
Bombus-oryginal-zlib-gg.jar
BombusFusion.jar
BombusHome.jar
BombusJETI.jar
BombusJimm.jar
BombusNimbuzz
BombusPanda.jar
aventlon.jar
bombusmodallplugins.jar
bombusmodnewmenu.jar
jabbim.jar
Bombusmod0.8.1407.500M
Bombusmod0.8.1400.497nm.id
Bombusmod0.8.1398.485M.id
Bombusmod0.8.1398.473M.id
Bombusmod0.8.1398.465M.id
Bombusmod0.8.1398.458M.id
Bombusmod0.8.1398.454M.id
Bombusmod0.8.1398.450M.id
Dollcellmod
Temoxmod
Temoxxmod
Dadollmod
Bombusmod
BombusMod 0.7 1.5.0 09 b03
Barepmod 0.7.1362.192 Monster
BarepMod0.7.1393.441M id
.7.1383.386M Monster nokia
Bombus Avalon.jar
Instango.jar
Instango-download-653.html
Instango-1626.html
Instango.htm
MJabber.jar
Mojabuzz.html
Mojab.jar
JabberMixClient.jad
Jmc.wml
Bluejabb
Bluejabb..
Bombus-NG.jar
Bombus-NG v434.zip
Bombus-NG v431.zip
Bombus-NG v430.zip
Bombus-NG v429.zip
Bombus-NG v428.zip
Bombus-NG v427.zip
Bombus-NG v422.zip
Bombus-NG v419.zip
Bombus-NG v414.zip
Bombus-NG v413.zip
Bombus-NG v409.zip
Bombus-NG v408.zip
Bombus-NG v407.zip
Bombus-NG v406.zip
Bombus-NG v402.zip
Bombus-NG v394.zip
Bombus-NG v393.zip
Bombus-NG v392.zip
Bombus-NG v388.zip
Bombus-NG v386.zip
Bombus-NG v385.zip
Search
About Me
- Ronik
- hi dear friends i m ronik a guy who feels that love never dies www.ronikrich.blogspot.com
Blog Archive
-
▼
2010
(212)
-
▼
November
(69)
- CHECKOUT NIMBUZZ AND OTHER USEFULL TRICKS / RONIKS...
- RONIKSITE DC APPS
- NIMBUZZ WEB FLOODER BY RONIK
- Certificate creater in 2 mins
- create-100-ids-online join roniksite
- Chat bot user Guide and installation process
- NEW-GPRS-TRICK
- AIRTEL LIVE
- Reliance Free GPRS Offer
- 500MB Free Internet for 6 Months
- FREE INTERNET FOR IDEA
- ANTIKICK ROOM TRICK
- Hack nimbuzz id by spying on cell phone
- Chating warrior 0.3
- Nimbuzz flood symbols tips and tricks.
- Hack nimbuzz chat room
- Top 10 Most Famous Hackers of All Time
- SETTING OF SKYFLOOD.
- How to Create a Fake Disposable Email Address
- Create fake id (email address)
- How to create a fake id
- Creating a fake login id
- leave your google search questions and stuff you w...
- Compile a C/C++ Program in Ubuntu
- How to Install C and C++ Compilers in Ubuntu and t...
- Easy Way To Hide Nimbuzz Room
- Baby Ngiler
- BOMBUMOD
- Mobile client new upload
- Bombus Edition For Nimbuzz
- New Baby killer(NFB)
- Sky Flood
- All secrets of bombus
- SETTINGS FOR MOBILE FLOODERS
- Nimbuzz updated new mobile flooders
- TATA DOCOMO 3G TARIFF ANNOUNCED !!!
- NIMBUZZ TRICKS AND TIPS
- Nimbuzz pc client
- Bombuz and Mobile Flooders
- STAYLISH NICKS AND FONTS
- New XML Scripts
- PLAY MOBILE JAVA GAMES ON PC
- NIMBUZZ CHATBOT
- NIMBUZZ PHONE SOFTWARES
- New PC flood softs
- Nimbuzz for pc with chatroom-Default nimbuzz
- Virus attack on Orkut fixed, says Google blog
- Orkut attacked by 'Bom Sabado' worm
- Can RockMelt (a new social browser coming tomorrow...
- World, Meet RockMelt
- Jolt Product Excellence Award: Development Environ...
- NAG Library for the Microsoft .NET environment
- Rigorously Tested Numerical Routines, NAG Library ...
- US Marines Shoot RROD’ed Xbox 360, Shouting “F#*% ...
- Microsoft releases F# under open source license
- Security firm protests Microsoft updates
- Microsoft Rolls Out Redesigned Dashboard Ahead Of ...
- Windows Phone 7 could hit HTC HD2 after all
- Windows Update Comes with Extras You May Not Want
- Twitter Updates Android App Buy “android” Black Fr...
- Facebook Updates User ID Policy, Puts Six Month Bl...
- Facebook Places To Change Status Updates Forever
- Facebook updates mobile platform, says 'no' to rum...
- The Socialite Network: UK's Queen joins Facebook
- U.S. cannot impose itself on Indo-Pak dialogue: Obama
- Obama a symbol of social justice: BJP
- Left parties hold demonstration Puducherry against...
- Maoists blow up school to protest Obama visit
- Remove the Blogger Banner
-
▼
November
(69)